 |
|
||
|
Transfer That File! |
| File transfer sounds like a very basic topic and it is. However, in this latest Newsletter article by Andrew Whitaker there is at least one nugget of information that will benefit almost everyone studying for a Cisco exam - from CCNA to CCIE. CCNA candidates will learn all they need to know about FTP and TFTP, two common ways to transfer files. The CCIE candidate will get a clear, concise refresher on the Cisco IOS naming convention. |
In this article, you will learn more about the IOS files and how to copy that file to and from your router via TFTP and FTP.
If you have ever had to upgrade your IOS, you know how confusing the IOS naming convention can be.
Because of the number of features that Cisco needs to support, Cisco has developed the concept of IOS trains. An IOS train is a vehicle for delivering releases that evolve from a common code base. With the addition of thousands of new features and a wide array of platforms, Cisco has to support multiple IOS trains with many different feature sets.
Types of Trains
| Train | Description | Examples |
| Mainline | Consolidates releases and fixes defects. Inherits features from the parent T train, and does not add additional features. | 12.2, 12.3 |
| T | Introduces new features and fixes defects. | 12.3T |
| S | Consolidates 12.1E, 12.2 mainline, and 12.0S, which supports high-end backbone routing, and fixes defects. | 12.0S, 12.2S |
| E | Targets enterprise core and SP edge, supports advanced QoS, voice, security, and firewall, and fixes defects. | 12.1E |
| B | Supports broadband features and fixes defects. | 12.2B, 12.3B |
Cisco IOS Software releases use the format A.B(C)D where:
A, B, and C are numbers.
D (if present) is a letter.
A.B is the major release.
C is the maintenance revision number. A higher maintenance number means more bug fixes. Any feature, bug fix, and hardware support available in a particular maintenance version are also available in the next one. On average, Cisco updates their revision numbers every eight weeks.
D, if present, indicates that the release is not a major release, but an extension of a major release. These extensions usually provide new features and new hardware support.
For example, IOS 12.2(3)T is IOS major release 12.2; maintenance version 3; technology release, which would implement new features and fix defects.
Sometimes you will see a number following the extension, such as 12.2(3)T1. The '1' indicates a rebuild on a mainline technology release train. You may also see a rebuild letter within the maintenance version, such as 12.2(3a)T, which would be major release 12.2; maintenance version 3; rebuild A; technology release.
Occasionally, you may see a Cisco engineering build designed for customers on a temporary basis to address a specific issue. An interim build, such as 12.2(3.1) has a train number plus a maintenance release number and a decimal number in parenthesis. The decimal number identifies the maintenance release (3) and the interim build number (1).
In addition, the Cisco IOS Software image is one of ED, XED, GD, LD, or DF:
ED stands for "Early Deployment." Early Deployment releases offer new feature, platform, or interface support. Most non-major releases contain ED releases.
XED stands for short lived, early deployment release. This is commonly called the 'X' release and will sometimes be designated by just an 'X'. It is the same as the early deployment release, but is designed only as an interim solution. If you need to use an early deployment release, choose ED over XED.
GD stands for "General Deployment." A major release of Cisco IOS software reaches the "General Deployment" milestone when Cisco feels it is suitable for deployment anywhere in customer networks where the features and functionality of the release are required. Criteria for reaching the "General Deployment" milestone are based on, but not limited to, customer feedback surveys from production and test networks using the releases, Customer Engineer bug reports, and reported field experience. Only major releases are candidates for the General Deployment milestone. To qualify as a general deployment release, the IOS has to meet the following criteria:
Customer Advocacy evaluation of known defects
No new features or platforms
No open critical issues
Minimal code changes
No previous serious defects in prior maintenance release
Comprehensive testing in Cisco's internal network
Extensive customer exposure
High level of customer satisfaction
LD stands for "Limited Deployment." A major release of Cisco IOS Software is said to be in the "Limited Deployment" phase of its lifecycle during the period between its first shipment and the GD milestone.
DF stands for "Deferred." DF releases are not available for downloading because of known defects. These should not be installed on your router.
When choosing a release, Cisco recommends a GD release when possible. Only choose an ED release if your hardware and software features leave you no other choice.
Understanding Cisco file naming convention is crucial for both CCIE and CCNA candidates. CCNA candidates should know the three main components of any IOS name:
Platform
Feature set
Memory Location
Now for all you CCIE candidates out there, you don't get it so easy. You need to know the IOS naming in greater detail. IOS names follow the format PPPP-FFFF-MM, where P = platform, F = feature set, and MM = memory location.
For example, if our IOS name were c2500-d-l.120-9.bin, then it would breakdown as follows:
| PPP (Platform) | FFFF (Features set) | MM (Memory location) |
| C2500 | D | l |
The last part indicates the IOS version, which, in this example, is 12.0(9).
The feature set identifies the feature contents on the router. Common feature sets include "j" for enterprise, "d" for desktop, and "s" for plus features such as NAT, ISL, and VPDN. Pay special attention to feature sets. At the CCIE written level, you are expected to be able to look at a common IOS name and know what feature set is running. This is expected not just for certification, but people in the workplace will expect this of you as well. While there are too many features sets to list here, here are the ones that are critical to know. These are based on a 2600 platform.
| Feature Set | Description |
| I | IP |
| IS | IP PLUS |
| J | Enterprise |
| JS | Enterprise Plus |
| JK8S | Enterprise Plus with IPSec |
The memory location indicates both execution area and, sometimes, the compression identifiers.
| F | Image runs in Flash |
| m | Image runs in RAM |
| R | Image runs in ROM |
| L | Image will be relocated at run time |
The compression identifiers indicate what type of compression is used on the image.
| Z | Image is Zip compressed |
| x | Image is Mzip compressed |
| w | Image is "Stac" compressed |
For example, image c7200-js-mz is an IOS for the 7200 series router, with enterprise plus software, executed in RAM, and is Mzip compressed.
Now that you understand the naming conventions, it is time to learn how to move IOS software to and from a Cisco device. This is a topic that you can bet will creep up in both the CCNA and CCIE exams.
The most common method of backing up and upgrading your IOS software is through the Trivial File Transfer Protocol (TFTP), which is defined in RFC 1350 (obsoletes RFC 783). Its name says it all; it is trivial in comparison with its more robust relative, FTP. Its trivial nature can be seen in the following limitations:
Runs on top of UDP (port 69), unlike FTP
Provides no user authentication
Cannot list directories
Limited header
TFTP uses a 2-byte op-code header that follows immediately after the IP and UDP headers.
Figure 4.
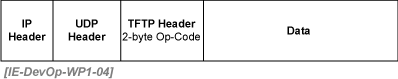
There are five types of operational codes:
RRQ Read Request
WRQ Write Request
DATA
ACK Acknowledgement
ERROR
If an error occurs, there will also be an error number given. There are three bits reserved for error codes, giving values 0 - 7.
0 - Not defined
1 - File not found
2 - Access violation
3 - Disk full
4 - Illegal operation
5 - Unknown transfer id
6 - File already exists
7 - No such user
TFTP is available on all Cisco routers and switches and is the most common method of backing up and upgrading the IOS on your devices. It is also used to make backups of your ever-critical configurations. You can make your router a TFTP client or a server. In this section you will learn how to:
Back up your IOS images using TFTP
Make your router a TFTP server
Before you can back up a file, you first need to know what file you wish to back up. This can be done with the show flash and show version commands. The show flash command will show you all of the IOS images stored in Flash, while the show version will show you the IOS that is currently running.
Router>show flash PCMCIA flash directory: File Length Name/status 1 9035592 c1600-sy56i-l.121-20.bin [9035656 bytes used, 3547256 available, 12582912 total] 12288K bytes of processor board PCMCIA flash (Read ONLY) Router>show version Cisco Internetwork Operating System Software IOS (tm) 1600 Software (C1600-SY56I-L), Version 12.1(20), RELEASE SOFTWARE (fc2) Copyright (c) 1986-2003 by cisco Systems, Inc. Compiled Thu 29-May-03 14:48 by kellythw Image text-base: 0x08048534, data-base: 0x02005000 ROM: System Bootstrap, Version 11.1(10)AA, EARLY DEPLOYMENT RELEASE SOFTWARE (fc 1) ROM: 1600 Software (C1600-BOOT-R), Version 11.1(10)AA, EARLY DEPLOYMENT RELEASE SOFTWARE (fc1) Router uptime is 12 hours, 32 minutes System returned to ROM by reload at 04:34:38 EST Wed Mar 3 1993 System image file is "flash:c1600-sy56i-l.121-20.bin" cisco 1604 (68360) processor (revision C) with 8192K/2048K bytes of memory. Processor board ID 10202938, with hardware revision 00972006 Bridging software. X.25 software, Version 3.0.0. Basic Rate ISDN software, Version 1.1. 1 Ethernet/IEEE 802.3 interface(s) 1 Serial(sync/async) network interface(s) 1 ISDN Basic Rate interface(s) U interface with external S bus interface for ISDN Basic Rate interface. System/IO memory with parity disabled 2048K bytes of DRAM onboard 8192K bytes of DRAM on SIMM System running from FLASH 7K bytes of non-volatile configuration memory. 12288K bytes of processor board PCMCIA flash (Read ONLY) Configuration register is 0x2102
To back up IOS, use the copy command. The syntax of the copy command is:
copy from to
While Flash is the most common source of IOS images, there are other places where files might be kept. You can copy an IOS to any of the following destinations:
bootflash:
disk0:
disk1:
flash:
ftp:
lex:
null:
nvram:
rcp:
running-config: (merges with existing configuration)
slot0:
slot1:
startup-config:
system:
tftp:
1600A#copy flash tftp PCMCIA flash directory: File Length Name/status 5148040 /c1600-sy56i-mz.121-20.bin [5148104 bytes used, 3240504 available, 8388608 total] Address or name of remote host [255.255.255.255]? 172.16.0.254 Source file name? /c1600-sy56i-mz.121-20.bin Destination file name [c1600-sy56i-mz.121-20.bin]?<Enter> Verifying checksum for 'c1600-sy56i-mz.121-20.bin' (file # 1)... OK Copy 'c1600-sy56i-mz.121-20.bin' from Flash to server as 'c1600-sy56i-mz.121-20.bin'? [yes/no]y !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Upload to server done Flash device copy took 00:01:24 [hh:mm:ss]
Have you ever heard the expression "Every rose has its thorn"? TFTP is no exception. While TFTP is easy and widely available, it still has to be secure from intruders. At no time was this clearer than with the Blaster worm that propagated throughout the Internet in the latter part of 2003. This worm was spread via TFTP, resulting in administrators everywhere locking down TFTP on their routers and switches.
There is an easy way, though, of securing TFTP access if the router is operating as a TFTP server. While you cannot use usernames and passwords, as you can with FTP, you can associate an access list to limit who can gain access to the router via TFTP. Begin by making an access list that defines what hosts can use the router as a TFTP server.
Router(config)#access-list 1 permit host 10.0.0.2 Router(config)#access-list 1 permit 192.168.121.32 0.0.0.15 Router(config)#access-list 1 permit 192.168.121.96 0.0.0.15
Next, configure the router as a TFTP server, but add the access list number to the end of the command. This is all you need to do -- and all you can do -- to lock down TFTP access to a router.
Router(config)#tftp-server flash:c1600-sy56i-l.121-20.bin 1
A new configuration option was introduced in IOS 11.3T that made networking professionals very happy. This option was File Transfer Protocol (FTP). For the first time, those configuring Cisco networking devices could use the features of FTP to back up and upgrade IOS images. This means that you can now associate a username and password. Now Cisco provides the option of configuring your router to act as an FTP server.
Before you read about configuring these options, you should first explore the nature of FTP. FTP runs on top of TCP ports 20 and 21 and is defined in RFC 959 (obsoletes 765). Port 20 is used to pass data and port 21 is used as a control channel. FTP can operate in either Active mode or Passive mode.
Every CCIE candidate needs to know the differences between these two modes.
In active mode FTP, only the control connection is initiated from the client. Figure 5 illustrates active mode FTP.
Figure 5. FTP Active Mode
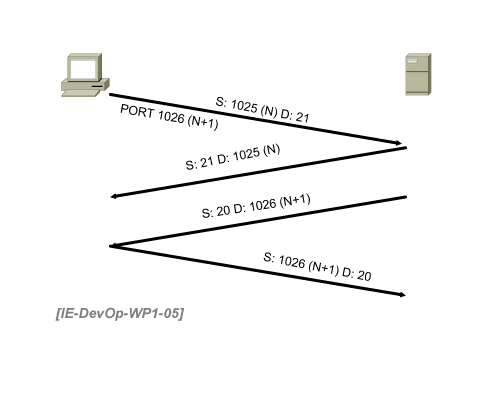
The FTP client begins by opening a control channel with a source port that is randomly chosen above 1023 (N) to the destination port of 21.
The FTP server responds with an acknowledgement. Commands are then exchanged between the client and server. The client sends the PORT command with N + 1, a return port that is one greater than the original source port.
After the PORT command is sent, the server initiates a data connection from the FTP data source port 20 to the client's data port (N+1).
The client sends an acknowledgement
Active mode is considered less secure than passive mode because the server initiates the connection back to the client. Because the server could be any host sending traffic from port 20 to a destination port greater than 1023, this presents a risk. Many firewalls have little means to prevent traffic coming from port 20 to any >1023 port on their attached inside networks.
In comparison, passive mode has better security. Both connections are initiated from the client. Figure 6 illustrates passive mode FTP.
Figure 6. FTP Passive Mode
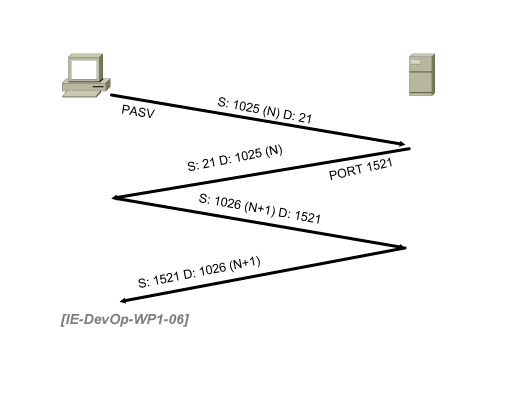
The client opens the connection with the source port above 1023 (N) and the destination port set to 21. This is no different from active mode at this point.
The server acknowledges, just as with active mode.
The client sends the PASV command.
The server responds with the source port of 21 and a destination port of a randomly chosen number above 1023. In our example, the port is 1521.
The client receives this information and opens up a connection to port 1521. It uses a randomly chosen source port or the original port number + 1.
The server responds and agrees to open the connection.
In passive mode, both control and data TCP sessions are initiated from the client. Because the client maintains control over the connection, the risk is minimized (from the perspective of the client).
The syntax for copying files is:
copy flash ftp:[[[username[:password]@]location]/directory]/filename
For Example:
Router#copy flash ftp:admin:[email protected]/cisco_files/my_IOS_file.bin
As an alternative to specifying the username and password within the copy command, you can also store them in your configuration. Use the following global configuration commands to set up your FTP username and password:
Router(config)#ip ftp username username Router(config)#ip ftp password password
If you do not configure a username and password in global configuration or when executing the copy command, it is assumed that you are using anonymous FTP (see RFC 1635 for more on anonymous FTP).
It is also possible to configure a router to act as a TFTP or FTP server. Other routers can then access that router and grab IOS or configuration files from it.
Configuring a router to act as a TFTP server involves only one step; you must specify what file(s) you want to host for other devices to access:
Router(config)#tftp-server flash:name
You can also use an access list to specify which devices can gain access to the router via TFTP. In the following example, only the host at 10.0.0.1 is allowed to TFTP files to and from the router, acting as a TFTP server.
Router(config)#access-list 1 permit host 10.0.0.1 Router(config)#tftp-server flash: c1600-sy56i-l.121-20.bin
Setting up a router to act as an FTP server involves two steps. First, you must enable the FTP server feature. Then you must specify the top-level directory. You do not specify individual files that are accessible through FTP, but instead specify the directory that FTP users start out in when they FTP into your router.
Router(config)#ftp-server enable Router(config)#ftp-server topdir slot0:
|